By: Neeraj Sab
Most of us have heard the saying “data is the new oil.” This is in recognition of the importance of data as a vital ingredient to improve any company’s profitability and competitive positioning. Just as oil helps machines run smoothly, secure and trusted data can help data owners or consumers remove friction from how data flows in their organization in order to extract greater value from their data products.
Based on my work with customers, it’s clear most data-driven organizations are planning to build data as a service (DaaS) architecture to make it easier to onboard their users, partners, and consumers of data, while moving the data in and out of cloud services. DaaS is a data management strategy which employs cloud infrastructure to store, integrate, process, and deliver analytics as a service through a network connection. Just like SaaS (software-as-a-service), DaaS removes the burden of locally storing, integrating, and processing data in the cloud; however, there are a number of technical challenges that can hinder efforts to build an effective DaaS strategy. When asked, data owners say these are the most common:
1. Finding known data elements in unknown locations — they know sensitive data exists somewhere in their data lake, but don’t know the exact location
2. Finding unknown data elements in unknown data — new data has arrived from partners, vendors, and other users, but they don’t know if it contains sensitive data
3. Applying the right tags to classified data
4. Devising a simple way to provide access to data tags
5. Encrypting data at rest based on the tags
To combat and solve these challenges, data owners need a centralized enterprise data protection platform to secure their data before exposing it to various users. A critical part of this includes data segregation in a controlled environment– and that’s where multi-tenancy comes into play. Multi-tenancy is not a new concept; it is a mechanism that enables multiple users of a product or an application securely–the operative word being secure. It is imperative to ensure one tenant (or user) is unable to see other tenants’ data if that tenant is not authorized to see it. Secure multi-tenancy also ensures data owners:
- Know who is accessing the data and from where
- Restrict or allow access to data from a single location independent of cloud provider
- Ensure data can be segregated out-of-the-box at various levels based on various tenants
- Enable data security teams to define data access policies and delegate management of data access to assigned data owners in the line of business or business units
- Ensure that data is encrypted at rest at the data attribute level
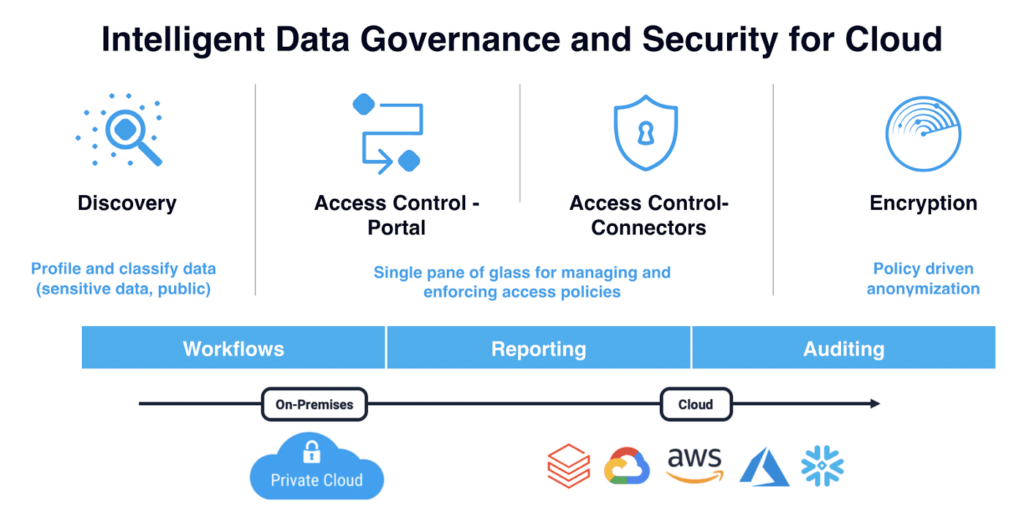
Components of DaaS Infrastructure
As companies build their cloud infrastructures, enterprise data architects strive to migrate data sourced from various heterogeneous, external data sources into cloud storage–which requires a horizontally-scalable solution that’s primarily API-driven and capable of discovering different data types on an automated basis.
After data has gone through the discovery process, it can be classified into different categories and tags can be applied to it. There are two main reasons to classify and tag data: first, it enables administrators to build data access controls based on the tags that are linked to a file, table, database, and column. Second, it enables administrators to encrypt data at rest, based on tags. Tagged data can also play a critical role in enterprises’ abilities to comply with regulations, such as right to be forgotten, data erasure, and more.
DaaS enables enterprises to move data in or out of the cloud, which exposes the data to various security challenges like authentication, authorization, or data encryption in transit (to name a few).
In order to address this risk, companies must encrypt their data at rest. Once sensitive data is identified, the easier it is to implement attribute-based encryption at rest, which is more fine-grained than file-, disk-, and volume-based encryption.
DaaS Trifecta
In most organizations, there is tension between external users and data consumers (e.g., data scientists or BI analysts) and IT personnel (security team, data engineers, etc.) IT teams want the flexibility to add new features without compromising performance and end-to-end visibility of user activity for audit purposes. Business and data users want an easy user interface and workflows that provide fast access to trusted data. Companies must build data security strategies that balance these needs.
Governance teams, however, cannot be forgotten in this balance. In order to meet their mandate, governance teams require access to various compliance workflows that can be called upon to perform operations, such as delete, mask, or quarantine sensitive data as mandated by GDPR, PDPA, LGBT, CCPA, and other industry regulations.
In order to realize the goal of achieving competitive differentiation through an effective DaaS strategy, companies need a multi-tenant environment with centralized enterprise data protection platform in place that includes automated discovery, classification, and tagging of sensitive data; consistent, effective user access controls and workflows; encryption capabilities to protect data at rest or in motion; and comprehensive auditing and reporting to comply with privacy regulations and industry best practices.
To learn more about how the Privacera Platform provides these capabilities from a single pane across all cloud service providers, visit / to learn more or sign up for a free 30-day trial.





