As organizations generate more data than ever before, it’s crucial to ensure that sensitive information is kept secure and accessible only to those who need it.
Enter attribute-based access control (ABAC), a powerful access control method that enables organizations to manage access to data.
Today, we’ll explore what ABAC is, how it works, and the benefits it offers for enterprises seeking to improve their data security and access control.
What is Attribute-Based Access Control?
Attribute-Based Access Control (ABAC) is a control method that is granular yet scalable across enterprises, allowing for the easy addition and removal of users. Since it determines access based on attributes, such as user/subject, resource/object, action, and environment, access is mediated around attributes associated with subjects (the requesters) and the final objects to be accessed.
The concept of ABAC appeared in the early 2000s. In December 2011, the US Federal Government endorsed ABAC as a recommended access control method for promoting information sharing between organizations. ABAC is an evolution of Role-Based Access Control (RBAC), with ABAC and RBAC being the two most widely known and used methods for access control. RBAC determines access based on a user’s role. In contrast, ABAC allows the use of additional attributes for more granular, fine-grained access control.
Attribute-based access control is a flexible and adaptable access control model that enhances data security, letting users create policies for data access structured around permissions-based attributes. ABAC controls allow for more nuanced command over access rights, providing superior authorization protection and easier scalability and management of roles.
How does ABAC work?
- First, attribute-based access control evaluates how attributes interact in an environment.
- Second, based on the policy, attribute-based access control then creates rules that determine access if specific conditions are met.
What are attributes?
There are four main categories of attributes:
- User/Subject Attributes
- Resource/Object Attributes
- Environmental Attributes
- Action Attributes

A real-life ABAC use case
Here’s an attribute-based access control example to illustrate how ABAC security works in real-life:
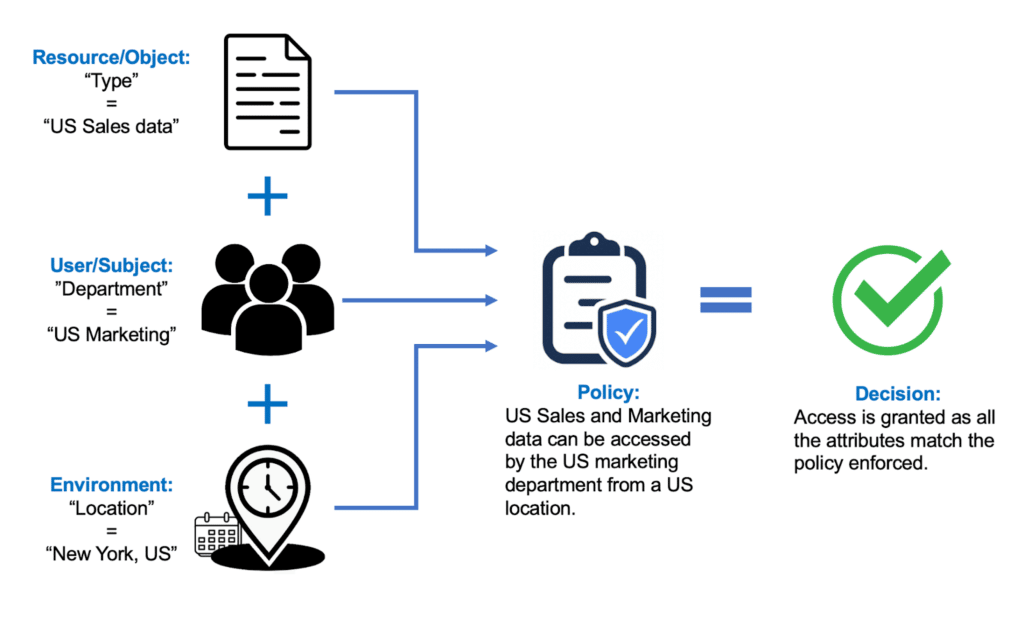
“If the user/subject is in the US marketing department, they should have read and write access to the US sales and marketing data, and their location while accessing data should be the US.”
Emily, a marketing manager in the US marketing department, requests access to the latest US sales data while working from the New York, US, office.
Here’s how the process works:
- An access request is triggered for the US sales and marketing data.
- ABAC evaluates attributes to determine if they match existing policies.
- If the attributes match the policy enforced, access is granted to the user.
In this case, Emily would be granted access to the data she requested because all the attributes match the policy enforced.
Now let’s say Emily is traveling to London, UK, for a week and tries to access the same data.
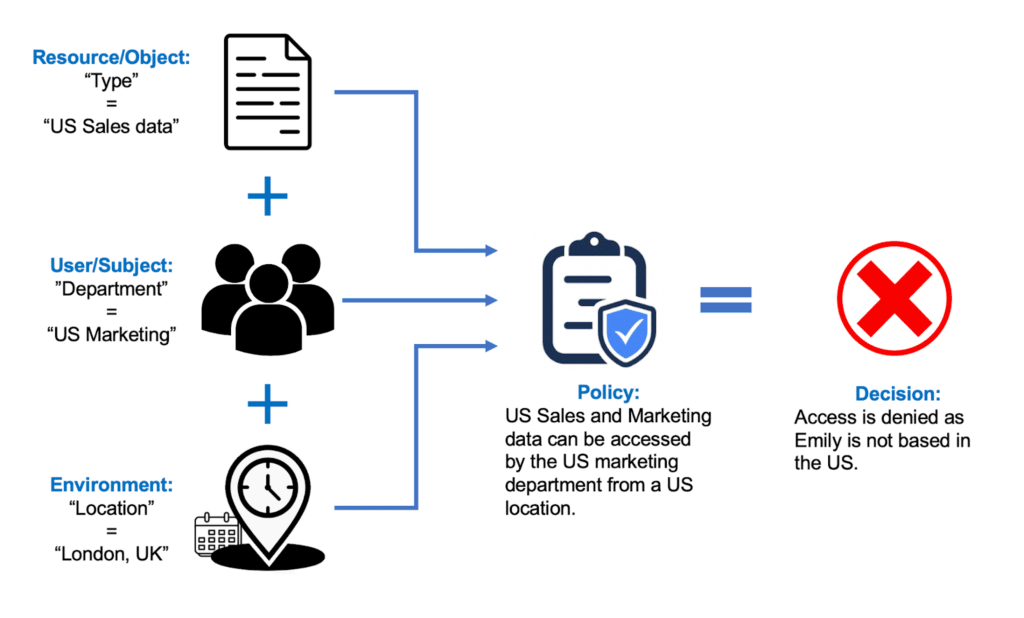
In this case, Emily would be denied access to the data she requested because her location while attempting to access the data did not match the policy parameter.
As long as the above policy is in place, an access request with the following attributes would NOT be granted access:
- User/Subject “Department” = “US Marketing”
- Resource/Object “Type” = “US Sales and Marketing data”
- Environment “Location” = “US”
Benefits of ABAC
Granular yet scalable: ABAC’s key benefit is scalability. Attribute-based access control allows for the widest range of users to access the greatest amount of resources without requiring any input from the admins.
For example:
- When a user joins an organization, they are assigned a set of user/subject attributes (for example, Emily is a marketing manager in the US marketing department).
- When a resource/object is created, it’s assigned attributes (for example, file with US sales and marketing data).
- The policy admin then creates an access control policy (for example, “US sales and marketing data can be accessed by the US marketing department”).
This one policy covers all the employees and the entire sales and marketing data in the organization.
Compatible with new users: As new users/subjects are added, they can be governed by the same policy, allowing them to access resources as long as they have the required attributes. This makes ABAC better suited to environments where users are constantly added and removed from the data platform.
Conclusion
ABAC grants the ability to enforce granular-level access control policies on a wide range of users and resources in a dynamic environment with little administrative oversight. This makes it highly suitable for large organizations. ABAC helps organizations effectively maintain access control, reduce time-to-data, and close security gaps while efficiently following regulatory compliance requirements.
See Privacera in action and learn more about ABAC and how you can implement it within your organization: request your demo.





