Security professionals today are focused on protecting their businesses from risks associated with breaches or non-compliant usage of organizational data. The traditional approach was to set your defenses at the perimeter or by practicing security by design on a system by system basis, but in a multi-cloud world those defenses are more or less ineffective. The data risks in this new world are multiplied as data democratization and the consumerization of the ability create new databases, data lakes, and making copies of data leaves vast repositories of unknown data sources and potentially unprotected.
A comprehensively designed data security posture management program aims to provide the tooling to manage the entire lifecycle from understanding your posture to remediating where gaps exist. Security teams need to gain insight into the location of data repositories, its content, the presence of sensitive data, and what controls are in place. Next, you want to match that with the actual usage patterns and then assess and prioritize the potential risks associated. The last mile in this journey requires the remediation of those risks through adding, adjusting or removing permissions, masking or encrypting the data.
Key Benefits:
- Unify the mandates of security, data, and infrastructure teams into a single platform
- Discover PII, GDPR, HIPAA, PHI Automatically
- Visualization and assessment of the desired posture vs the actual risk posture
- Protect Data Across Data Systems and clouds
- Continuously audit and monitor
Complete DSPM solution
Most DSPM solutions today focus on the discovery and assessment of the risk posture and again leaving the remediation or pro-active controls to some IT ticketing process with admin or data engineering staff in the background to implement the controls.
A complete Active Data Security Posture Management solution brings all of this together into a single data security platform that unifies the following core elements
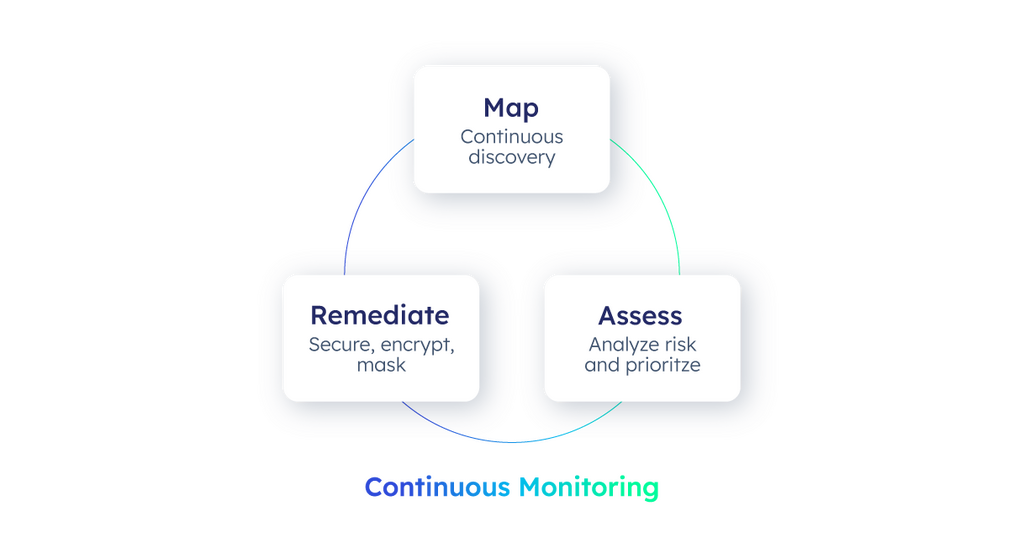
Map your data estate
Automatically discovery and scanning of data repositories, both structured and unstructured for the presence and location of sensitive data using built in classifications rules, expressions and machine learning models. The visualization should combine our sensitive data view with the presence of access controls as well as the actual usage patterns detected from these various data sources. This sensitive data map view provides a single pane of glass for security teams to understand and assess their entire data estate and the security and privacy posture in place.
Assess your risks
The second part of our lifecycle is to analyze the results from our mapping exercise to deeply determine risks, gaps or suspicious access patterns and highlight these risks in dashboards, alerts and notifications. In addition, the security teams need to be able to define KPIs to report on progress of strategic programs and how the overall posture rating is trending over time. Many organizations are moving to a zero trust framework and employ a principle of least privilege access to define access permissions. This will limit the number of data sources or files someone has access to to the exact data sets they need to do their jobs. Over-provisioning of access is a leading contributor to the severity of data breaches when credentials get compromised.
Remediate the gaps
The third part of the lifecycle is to actually implement the system controls for data access, masking and encryption across the entire data estate. These could be instituted as a proactive mandate or the remediation of a detected gap in our posture. The typical process of IT tickets and manual data access controls being implemented one system at a time leads to inconsistencies, risks and delays. Providing direct and automated integration between the Mapping, Assessing and the Data Access Governance layer is pivotal to streamline this process and ensure the enterprise can scale on both their needs to improve data democratization as well as reduce their risk and exposure.
Continuously monitor and audit
Data security posture management is not a one and done process and requires constant execution of our lifecycle and monitoring and audit for drift to keep adjusting our guardrails and system controls.






