As enterprises race to become data-driven businesses, a latent tension is intensifying: is data the “new oil”? A “toxic asset”? Both?
Whichever metaphor you would like to use, what is certain is that no organization will survive the twenty-first century without optimizing the use of its data assets. Similarly, cybersecurity, privacy, and compliance risks increasingly present huge challenges that require well-developed strategies and the appropriate tools to address them.
The emerging field of “infonomics” highlights how organizations must effectively manage, measure, and monetize the information at their disposal to drive growth and remain competitive. Just as with software development, however, using data safely and within organizational and regulatory risk tolerances is critical. Putting this information to work – which enterprises absolutely must do in order to deliver value and ultimately continue their existence – requires that the appropriate safeguards are in place.
The competing mandates between Chief Data Officers – focused primarily on putting their data to work as quickly and efficiently as possible – and Chief Information Security, Privacy, and Compliance Officers – who seek to minimize the risk of doing so – can seem irreconcilable. To untangle this Gordian Knot requires bold action, in the form of implementing an effective Data Access Governance and Security program.
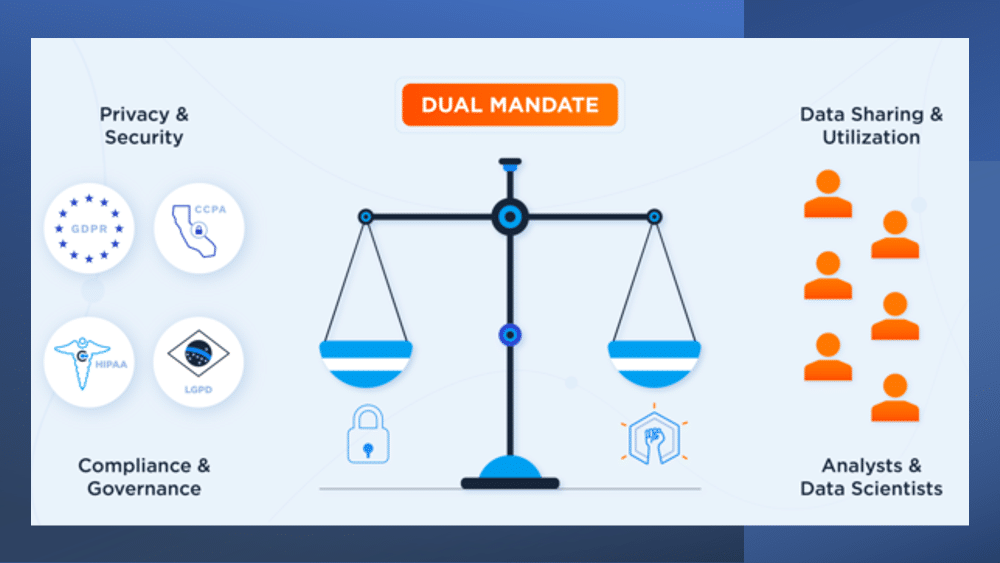
Data Access Governance and Security comprises the policies, procedures, tools, and techniques necessary to manage the risk posed by data and its utilization, whether at rest, in motion, or in use. Effective platforms can do this throughout the entire data lifecycle while at the same time driving infonomic growth by allowing the right people to access the right information at the right time.
Policies and Procedures
Effective Data Access Governance and Security start with developing the correct policy framework for responsible data use. The inputs can include legislative or other regulatory requirements such as the European Union’s General Data Protection Regulation, industry certifications and attestations such as the System and Organization Controls (SOC) 2 standard, and the business’s internally-identified tolerance for contractual and reputational risk stemming from the use of its data sets. Wholly eliminating risk while delivering infonomic value is impossible, so organizations need to analyze and document how much they are willing to accept. Comparing this risk to the potential benefit of the products or services they offer is a reasonable way to do so.
With the philosophical underpinning for Data Access Governance and Security in place, implementing it through effective procedures is the next step. Although security and compliance professionals can assist in building the correct framework, it is business-line executives who must serve as data owners. These individuals, who understand both the inherent power and risk of the information they maintain, are best positioned to make decisions regarding access management. These leaders must be able to seamlessly authorize data for inspection and analysis while also maintaining non-repudiable audit trails to ensure accountability. With these capabilities, they can make the correct decisions regarding the appropriate tradeoffs between data risk and infonomic growth.
Once provisioned and authorized, it is up to data users – the analysts, marketers, and data scientists – to transform raw information into valuable and actionable insights. Only when they seamlessly get access to the right data can enterprises kick infonomic growth into high gear.
Tools and Techniques
In order to implement the aforementioned procedures and policies and safely power rapid infonomic growth, enterprises need the correct tools. Comprehensive Data Access Governance and Security platforms facilitate this through identifying and classifying sensitive data, controlling access to it, as well as encrypting, masking, and expunging it in accordance with established organizational policies and procedures.
As a first step, discovering exactly what data an organization maintains is often easier said than done. Large enterprises can operate tens of thousands of different data assets, each containing different types of information. Machine telemetry from manufacturing operations might have serious competitive risk associated with its unauthorized disclosure, but no privacy or regulatory concerns. Conversely, customer social security numbers might not have any business use but their leak could lead to massive government-levied financial penalties. An effective data discovery tool will be able to tell the difference between these things using dictionaries of known keywords, pattern matching techniques, and heuristic frameworks. Once identified, a corresponding tagging system can flag data for subsequent processing.
When sensitive data is correctly marked by an effective Data Access Governance and Security solution, data owners can then apply granular controls to the information. Using their business understanding to control and understand who has access to which data and why, they can manage risk based on the organization’s policies while maximizing its infonomic potential.
Finally, data masking, encryption, and expungement are all features that a Data Access Governance and Security product must be able to deliver. To ensure customer, partner, and employee privacy, data owners should be able to redact sensitive information at a granular level to ensure that only entries with business value are exposed for analysis. Similarly, using industry-standard encryption to protect this data at rest is another measure that can help to minimize risk while maximizing infonomic potential. Finally, purging private information from organizational systems when it no longer has any business or regulatory requirement to exist should be the final step in the data lifecycle.
Conclusion
To remain infonomically competitive, enterprises will need to manage the risk posed by their sensitive information through effective Data Access Governance and Security. Risk will always remain, and cutting-edge organizations must accept a certain amount as part of their operations. With that said, an effective Data Access Governance and Security program – with the right policies, procedures, tools, and techniques in place – can minimize this risk while still allowing for rapid growth. Those enterprises able to do both will emerge as the most successful and dominant ones of the current century.
Learn more about Privacera here, or contact us to schedule a call to discuss how we can help your organization meet its dual mandate of balancing data democratization with security to maximize business insights while ensuring privacy and compliance.





