Our customers continually credit Privacera for helping them ensure data privacy and compliance for data distributed across on-prem and cloud platforms. As users of our technology, they are creating a holistic, petabyte-scale data access control system that simultaneously supplies data scientists and analytical teams with the data they need.
However, we wanted to find out what others think. Are technical leaders who have not heard of Privacera feeling the pressure to comply with privacy regulations such as GDPR, CCPA and LGPD? Are enterprises concerned about how they will need to adjust their enterprise data architecture to meet the demands of consumers pushing for increased governmental oversight and regulations to their digital footprint?
70% say privacy regulations make it more difficult to migrate analytic workloads to the cloud
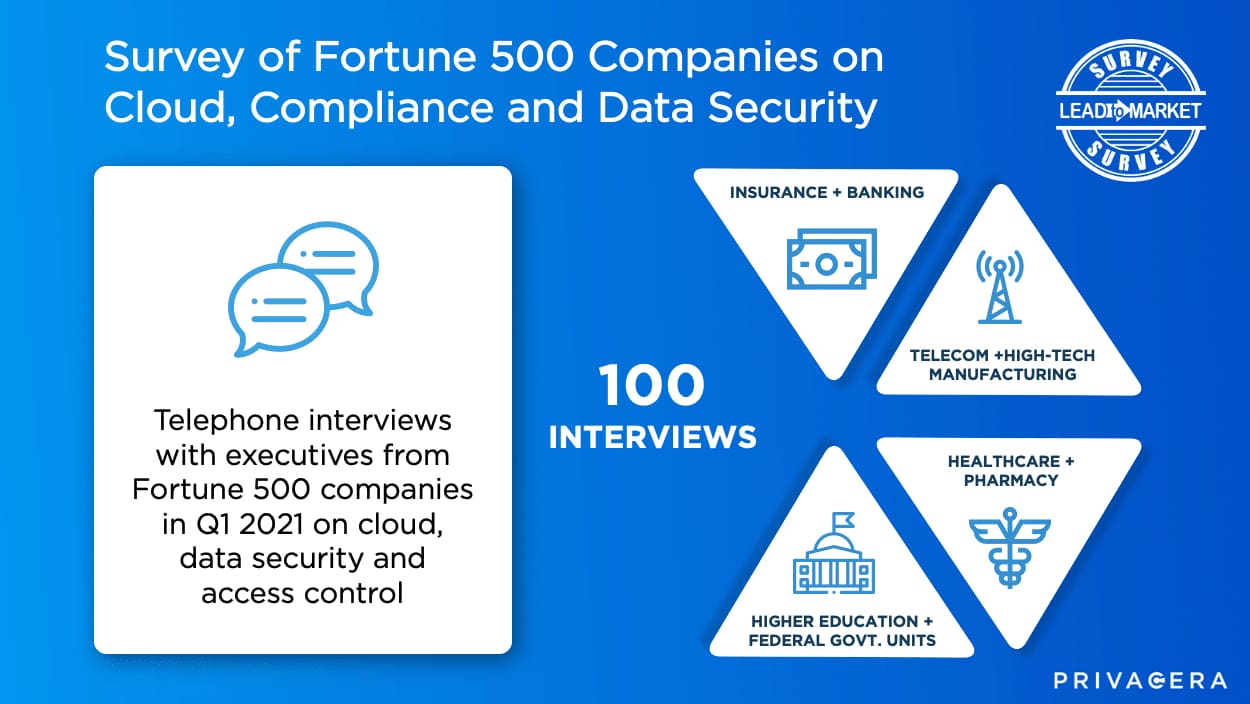
In Q1 2021, we commissioned a survey to understand how 100 Fortune 500 leaders responsible for data access control and permissions for cloud-based storage and analytics systems felt about cloud usage, compliance and security. What we found was that the overwhelming majority (70%) said that privacy regulations made migrating analytics workloads to the cloud more difficult. This is understandable as each cloud service offers up its own unique controls for data security. Because there is no consistency among providers, enterprises that deploy multiple cloud systems are left with a convoluted and highly fragmented security landscape.
Consumer demands and governmental regulations are forcing enterprises to increase control of their customers’ digital data. As a result, analytics, data architecture, IT and security teams all need to come together and consider a different paradigm.
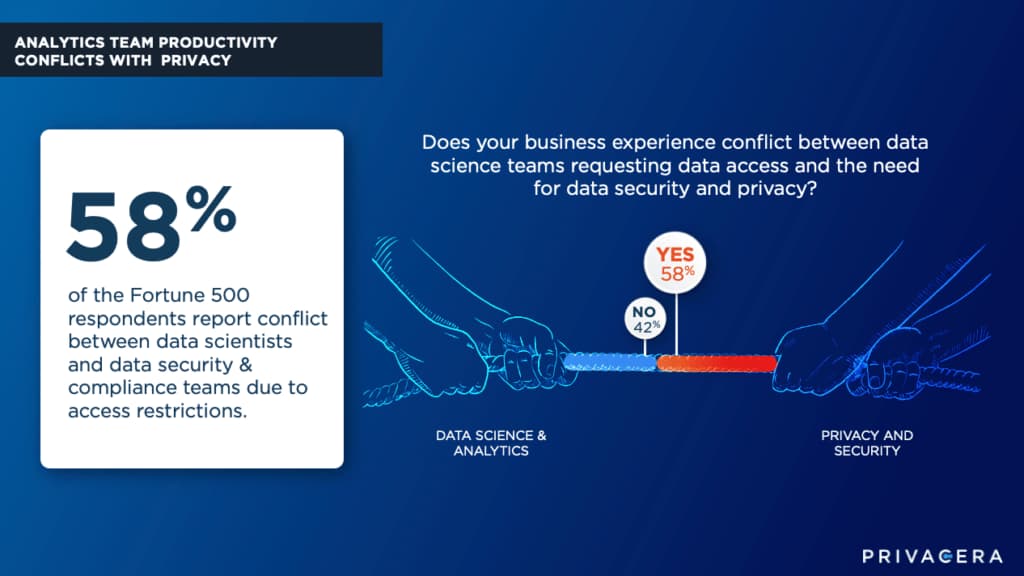
In fact, current pressures are already creating friction, with 58% of survey respondents reporting a conflict of interest between analytics and security. An analytical teams’ productivity is adversely impacted by security requirements, often resulting in a never-ending, and difficult to resolve, stream of IT tickets requesting access to sensitive data. These security requirements are impairing analytics teams from doing their jobs, either by delaying or even denying access to the data necessary for modeling and analytics.
Some respondents deploying a layered security approach
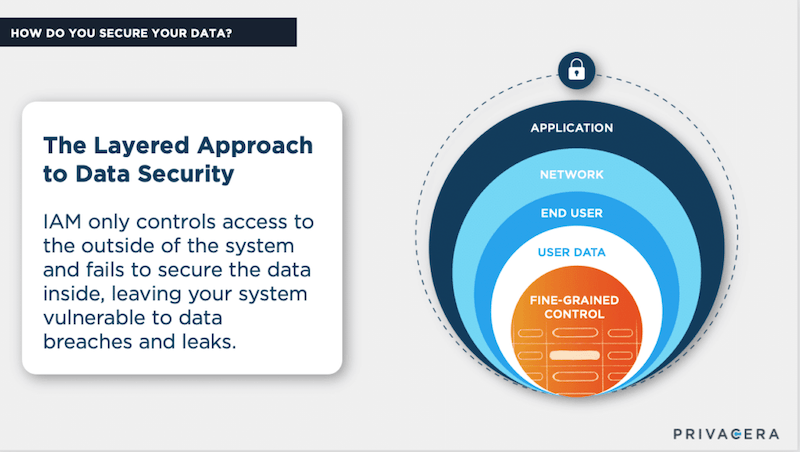
While a majority of the survey respondents do utilize IAM technology (Identity and Access Management) tools, it was not the only tool utilized to ensure data security. Deploying a layered security approach, some respondents recognized the need to reduce information risk by enabling data analytics with much more granular data access control.
Typically, security tools provide controls at the application, network or end-user layers. Yet, in today’s zero-trust networks that is not sufficient. As recent data breaches have proven, once a bad actor has gained access to the data storage or analytics system – every piece of information stored within is accessible. This is exactly what happens when IT or security teams grant data science teams blanket access to data – it creates a massive hole in the security perimeter. Worse, it violates the privacy and compliance regulations that were created to protect the personal digital rights of consumers in the first place.
A more granular, more surgical approach is needed, and some survey respondents have adopted additional technologies such as encryption and masking, as well as fine-grained access control and row/column filtering. The fine-grained access control enables an almost surgical level control of data access, enabling analytics teams to access the precise data set they need. No more and no less. This upholds the corporate obligation to adhere to legal requirements, without impeding the productivity of data scientists.
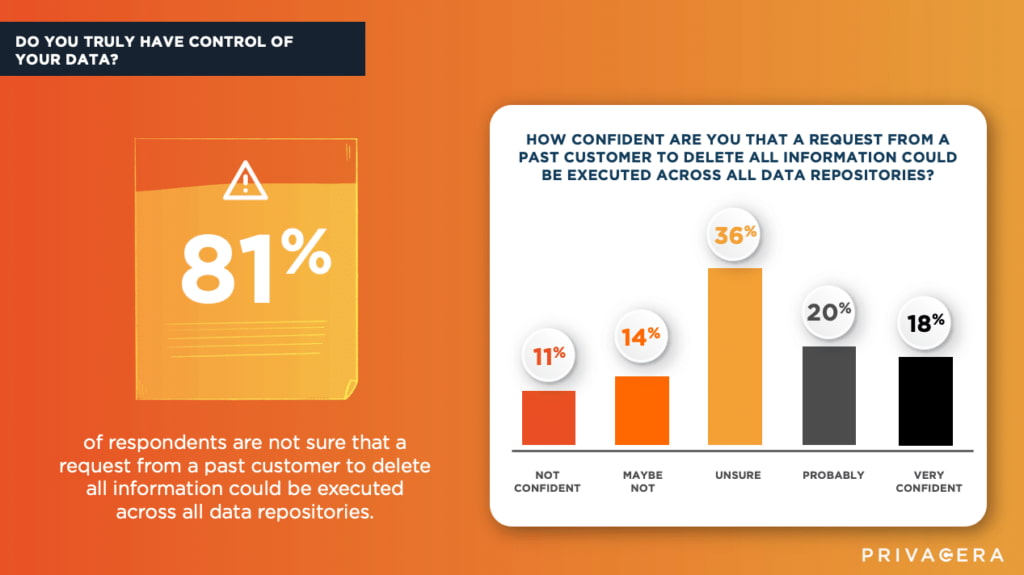
81% not confident PII deletion could be successfully executed across all data repositories
As privacy regulations continue to increase around the world, enterprises have no choice but to adopt new measures to manage data security and privacy. For instance, 81% of survey respondents were not confident that a request from a past customer to delete all information could be successfully executed across all data repositories. Clearly, this is not satisfactory where most privacy regulations require this capability, leaving enterprise IT teams holding the bag on figuring out ways to meet their obligations.
How are companies currently managing privacy requirements?
The final portion of the survey addressed this very issue. For those faced with the complexities of the problem, we asked how they are coping and what approaches they are taking. Survey respondents shared how their respective companies currently manage different privacy requirements such as anonymization of data and RTBF (Right to be Forgotten), what tools they currently have in place, and what they expect they will need tomorrow. Their responses mirror the pain found in most organizations today and create a benchmark for current best practices and future predictions. We look forward to measuring the industry’s overall approach to creating a practical solution that enables analytics teams to access data without compromising compliance.
To see the results of the survey, please register your interest here.