Today, to ensure organizations are compliant with regulations of various industries and geographies, encrypting data at rest is essential. For example, healthcare organizations must comply with HIPAA. Banking and payment organizations must comply with various regulations and standards, including PCI DSS, SOX, and GLBA. Retailers storing customer data are also required to follow privacy regulations in order to minimize customer impact in the event of a security breach. In addition to industry-specific regulations, geography-specific regulations — such as GDPR in Europe, CCPA in California, LGPD in Brazil, and PCPD in Hong Kong — have implications well beyond their specified borders. GDPR, for example, may appear to be Europe-specific on the surface, but organizations conducting business in Europe in any capacity (e.g., airlines flying European customers) are required to comply with GDPR.
This blog will analyze the three different levels of encryption, why they are needed to protect your private data against attack vectors, and their specific use cases.
Let’s start with a simple question: Why not encrypt all data on the network, so we’ll have the protection we need? The answer is a challenge: because we will not be able to do analytics on the encrypted data and extract insights from the data to drive business value (e.g., optimize supply chain, reduce customer churn, provide more services to customers at no additional cost, reduce fraud, and more).
Challenges in Data Encryption and Security
When discussing data security, the top challenge we are faced with is to secure data on one hand and enable access to protected data for analytics on the other. So, what’s the solution?
It is essential to enable data scientists and analysts to read data in order to gain insights, drive business value in the form of marketing optimization (e.g., targeted campaigns), focus on sales growth, and optimize business efficiency to lower operational costs. While data can help achieve these goals, securing data is equally important to remain compliant with regulations, prevent hefty fines, establish customer trust, and increase brand value.
Ideally, both security and analytics should be prioritized; however, when faced with the challenge of ensuring security or performing analytics to extract insights, companies prioritize security at the cost of limiting access to data, due to inadequate controls — leaving business value in millions of dollars that can be realized using data.
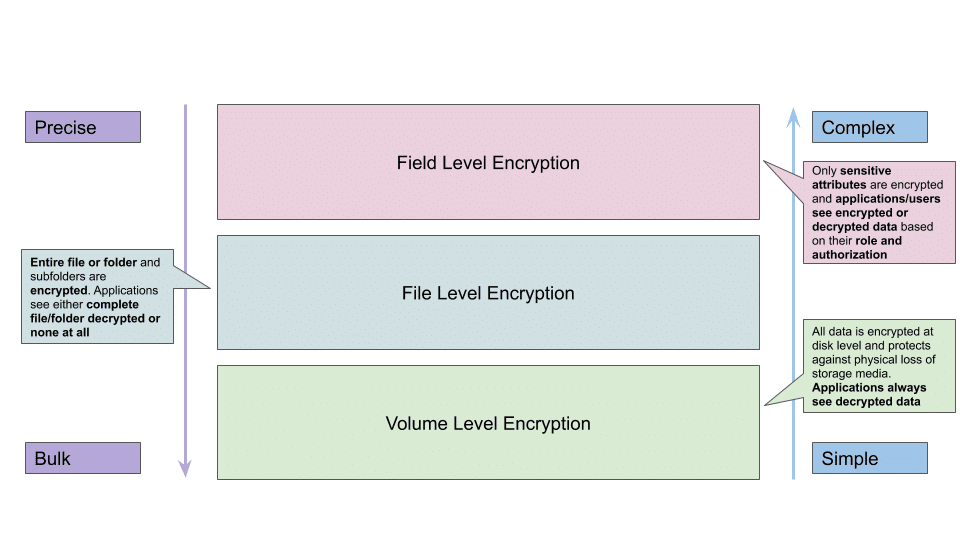
Encryption is one dimension of securing data. We can encrypt all data and it will be secure, but encrypted data is not useful to drive insights. Let’s look at the three levels of encryption and how they protect you:
- Full volume or Transparent Data Encryption
- File or Data zone Level Encryption
- Attribute or Field Level Encryption
Transparent Data Encryption
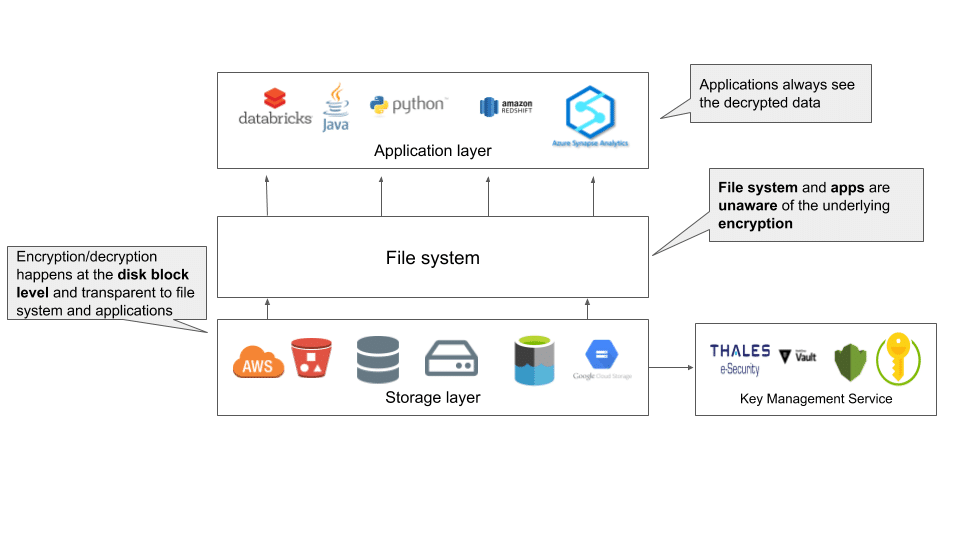
The first level of encryption is transparent data encryption (TDE), or full volume encryption. It works by encrypting all data on a disk. In Azure, for example, TDE can be enabled using the Azure Storage Service Encryption (SSE). When client applications read data, Azure SSE simply decrypts it before returning the data. Performance overhead of this encryption level is minimal, as it occurs below the file system level and the entire disk is encrypted. As such, decryption and encryption key management is done by Azure. On AWS, a similar service, Server Side Encryption (SSE-S3), can be used to encrypt all the data on disk.
So, how does this level of encryption protect you? TDE protects against unauthorized access of data in case a physical disk is lost. For example, if your laptop is stolen at the airport, TDE prevents a malicious actor from decrypting and reading your data. It may seem that TDE has little value at the data center level, as the chance of someone stealing and physically walking away with your disk is low; however, in the case of data centers, a more likely scenario is improper disposal of old hardware, which can result in unauthorized users getting access to your data — which is why full volume encryption, at rest, is required to ensure compliance with PCI DSS, GDPR, CCPA, HIPAA, and several other regulations.
File or Data Zone Level Encryption
Full volume encryption protects in the case of physical loss of storage media, but it cannot protect sensitive data at the consumption level. Because encryption/decryption happens below the file system level, all applications and users get the decrypted data, which leads to sensitive data being exposed to all the applications and users reading the data. To protect sensitive data, organizations can use file-level encryption to encrypt the whole data file. An extension of this type of encryption is zone-level encryption, where an encrypted zone is created and all folders, subfolders, and files are encrypted within the zone. File or data zone level encryption allows enterprises to encrypt data for all users and set policies for authorized users who can then run analytics on the decrypted data.
Because this level of encryption affects the whole file, only authorized users are allowed to see the decrypted data, as files cannot be partially decrypted. For example, if a data file contains SKU, quantity ordered, price, customer name, and address, anyone who sees the file will see all five attributes. It is not possible to selectively encrypt only a person’s name and address, which means anyone who isn’t granted access to the sensitive information cannot use the data to generate insights.
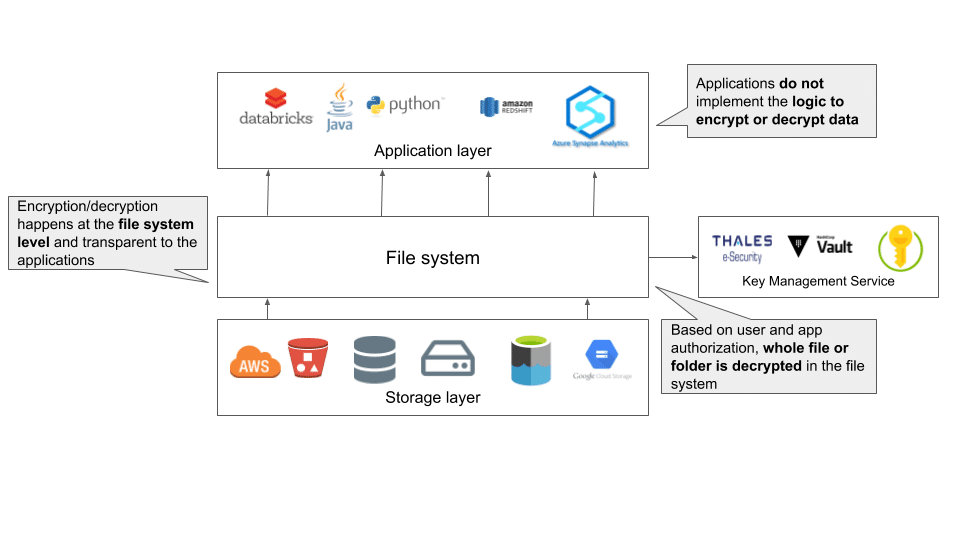
File or data zone level encryption is useful when sharing data in and outside of the organization, as encrypted files or folders can be sent separately and keys shared securely to decrypt files. This ensures no malicious actor will be able to decrypt files and access the contents. It is recommended to use separate keys for different files, folders, and zones and manage them in a key management system that is secure.
Attribute or Field-Level Encryption
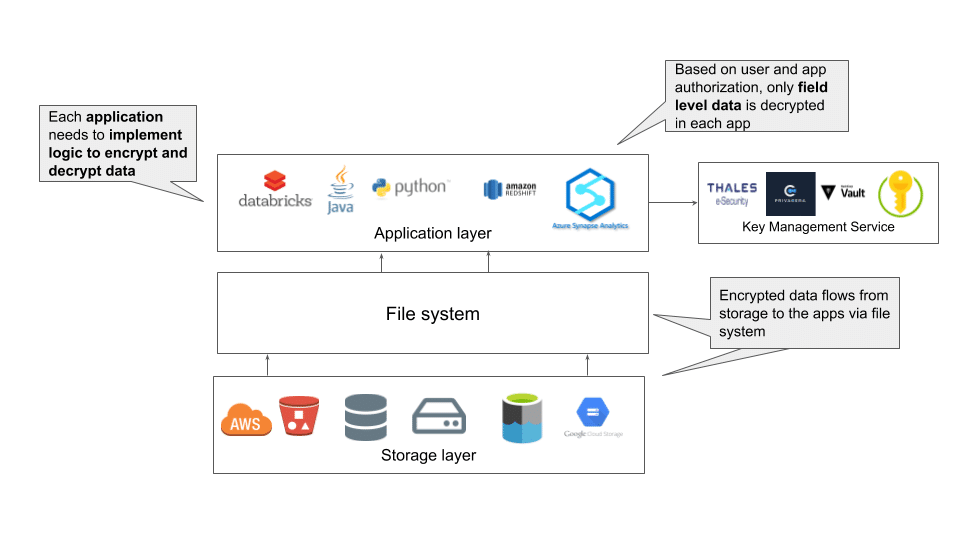
Attribute or field-level encryption is the most granular form of encryption. The process allows you to selectively encrypt only sensitive data in a file or a database. Implementing attribute-level encryption enables organizations to encrypt only sensitive information and open up the data for advanced analytics to the larger organization without compromising data compliance requirements. Sensitive data is decrypted only for select users based on their roles. In addition, attribute-level encryption provides algorithms — like format-preserving encryption (FPE) — to support analytics on encrypted data, opening the analytics to the entire organization without the risk of exposing decrypted data.
Attribute-level encryption is harder to implement, as application-level encryption and decryption must be supported. Authorized users from a supported application can see the decrypted data, while the data remains encrypted for all other applications and users.
Throughout various industries and geographies, organizations must navigate new attack vectors and risks associated with protecting their sensitive data. The three fundamental encryption methods (full volume encryption, file- or data zone level, and attribute- or field-level) are critical in order to protect data against these attack vectors and serve different purposes for different use cases. To ensure comprehensive visibility and control of sensitive data, organizations should adopt all three encryption methods to enable the safe access of their data across their enterprise, while maintaining stringent compliance with the various privacy regulations and standards.
Privacera helps customers encrypt data at the field and attribute level, enabling data science and analytics teams to utilize more data to build models and extract insights to drive new business opportunities, leading to increased customer satisfaction and optimized business efficiency. To learn more about how Privacera can help you encrypt the data at the field level, please contact us.





