The Charter Fit
Effective CISOs are focused today on protecting the business, satisfying board and investor expectations, and aligning themselves with organizational priorities. As little as 3 years ago, conversations with CISO mostly focused on perimeter concerns. Data access or what resides inside the firewalls were of less concern and usually directed towards IT. The transformation of our data centers into cloud estates is rapidly changing that.
Having been involved in the security space for more than a decade, I believe that data posture management plays a crucial role today in simplifying the CISO’s job by aligning risk reduction goals and providing clear progress indicators. Specifically, it enables CISOs and their teams to manage unknown or dark data. This is a crucial context, as it directly impacts CISO priorities.
Data risk is a growing critical concern, especially when it comes to unknown data. Let’s face it, unknown data is a significant risk because it’s what attackers want. The real threat today lies in data, not just systems, across multi-cloud and hybrid environments. The key issue has become unknown data in a cloud service provider, as anyone can spin up an instance, making it a prime target for bad actors. For this reason, today’s CISOs should aim to prevent data breaches by focusing on safeguarding or mitigating these risks, ensuring their organization’s data is secure. Let’s face it, security is fundamentally about managing risk, and this risk is likely way higher than it should be. To win, security teams need to outsmart cybercriminals who focus on exploiting data vulnerabilities. This isn’t just about threat analysis; it’s about actively managing risk and staying ahead of the game.
Data Posture Management Thinking
The proliferation of data across cloud service platforms and geographic boundaries has created the need to discover and locate disparate data repositories containing sensitive data at scale. I believe that a significant driver of this requirement is a recent SEC ruling that mandated organizations report material cybersecurity incidents promptly. Organizations must file an 8-K for material incidents and have four business days to determine whether a detected incident is material.
CIOs we have talked to are candid that determining materiality today requires a significant amount of time and forensic effort because they do not necessarily know what is stored where and whether it is potentially material. This makes it critical to find where high volumes of sensitive information are stored. At the same time, the SEC wants to see public organizations prove they are doing more to prevent material incidents. Consequently, organizations must file and share how they have mitigated a growing array of data security and privacy risks.
The fact is that the move to cloud service provider architecture has accelerated business innovation and, in many cases, improved security over aging data centers. However, it has also led to data proliferation that is unknown or undiscovered across cloud service providers. This issue can spawn infrastructures and data repositories that are rarely used or obscured, making organizations more vulnerable.
While security teams can be tasked by business or compliance leaders with protecting specific data repositories and pipelines, some sensitive data locations can remain unidentified. This matters considering Verizon’s 2023 Data Breach Investigations Report found that data breaches accounted for 5,199 incidents and 16,312 security incidents. This underscores the urgent need for technologies capable of unearthing hidden or dormant data repositories and assessing their exposure to risks concerning data residency, privacy, and security.
Defining A Complete Solution
Data Security Posture Management is emerging as an umbrella construct to help visualize and understand our possible risk, but also to orchestrate the remediation or pro-active implementation of systematic controls across the entire data estate. In this regard, I believe the complete solution will have to orchestrate a lifecycle that would start at Mapping the entire data estate in terms of data locations, sensitive data present, usage patterns, Assessing the risks associated, and Remediating by implementing or adjusting controls automatically. All this of course needs to be underpinned by Continuous Monitoring.
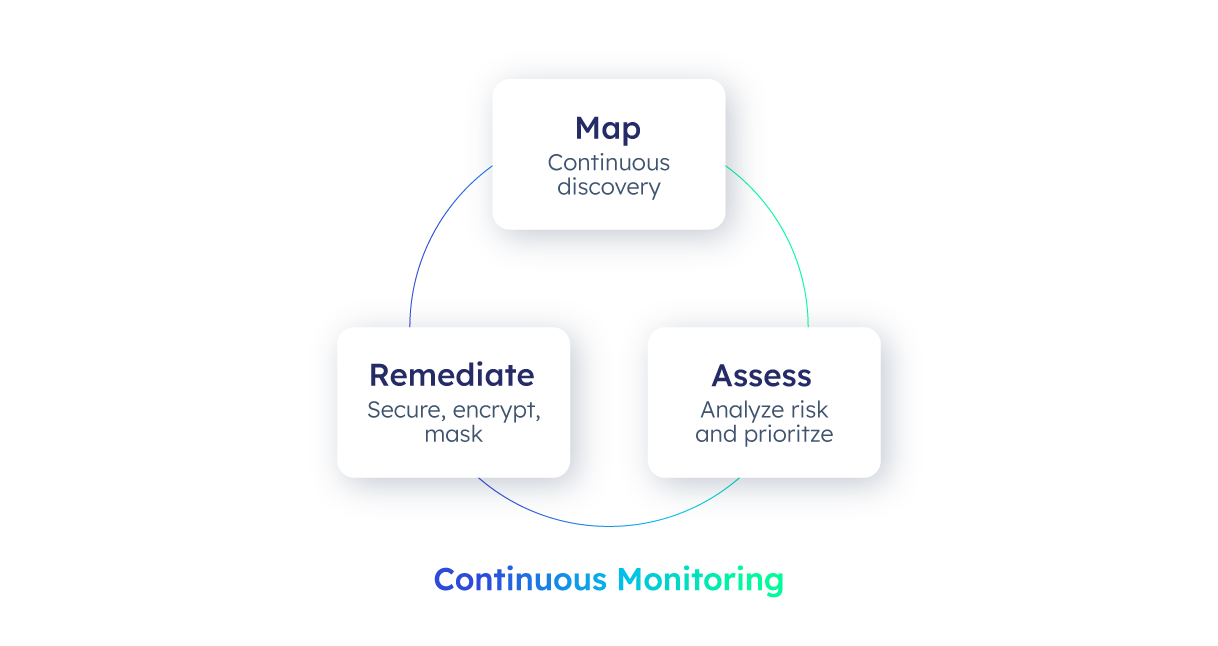
Map
I believe that an effective solution starts by visualizing an organization’s sensitive data posture. It achieves this by discovering and visualizing the presence of sensitive data, provisioned privileges, and access patterns across a hybrid data estate. Next, it creates a sensitive data map showing the location of structured and unstructured sensitive data, who has access to it, who is accessing it, and the associated business risk from all three. This comprehensive view enables organizations to manage their data risk effectively.
Assess
Next, the solution should enable organizations to assess the risk impact of their current data security posture. The solution should do this by identifying inappropriate data usage that needs rectification by displaying over-provisioning and recommending policy and control fixes—I like to call these steps active posture management. Here, you want to match access and usage patterns with access provisioning and integrate posture data with existing security tooling, including security analytics platforms such as SIEM. By taking a holistic approach, the solution can ensure continuous alignment between data security practices and organizational policies. Next, I believe the solution should enable organizations to assess the risk impact of their current data security posture. This should include identifying inappropriate data usage that needs rectification by displaying over-provisioning and recommending policy and control fixes.
Remediate
A posture management solution as a goal helps organizations mitigate, secure or actively remediate, monitor, and audit risks. Active and in most cases, automated remediation, includes taking sensitivity data access policies and tags and creating controls across data lakes and datasets discovered, ensuring seamless control across expanding data estates.
By adding data access management and control to data security posture management, aligning with the IT principle that simplicity breeds efficiency.
Importantly, moving from system-specific controls to a comprehensive approach ensures transparency, consistency, and auditability, transforming organizations from a relentless game of Whac-A-Mole into a more efficient and secure state. Piecemeal approaches to security by design consume valuable, often scarce engineering resources on non-value-add processes and suffer from opacity and limited control, hampering compliance. These approaches stymie the organizational capacity to manage security and access policies uniformly across analytics platforms, challenging the assurance of consistent security and governance. Adopting an active, unified data security governance model drastically streamlines the administrative load and enhances the ability to meet rigorous compliance mandates.
Continuous monitoring
Another important capability of posture management solution should be the ability to continuous monitoring and auditing. This ensures the continuous management of the entire process by meticulously maintaining a detailed audit log of every data access event. This log captures who accessed which data, when, and under what protections—be it transparent, masked, or encrypted. This wealth of information isn’t just for record-keeping; it should be designed for integration with data security analytics tools. This enables real-time alerts and monitoring to enhance data analysis capabilities. In the end, this should not be just about tracking data access; it should be about proactively safeguarding your data.
Parting Words
As we have discussed, active data security posture management (DSPM) streamlines data security by enabling organizations to discover, assess, and mitigate risks efficiently in a continuous lifecycle. It unifies security governance, ensuring consistent compliance across platforms, while continuous monitoring and detailed audit logs enhance real-time data protection. By integrating with data security analytics tools, data security posture management it not only tracks data access but proactively safeguards it, transforming security management from a resource-draining challenge into an efficient, compliant, and transparent process.





