Gartner has released a series of insightful reports over this year regarding data security governance, offering critical guidance for organizations navigating the increasingly complex landscape of data protection. In this summary, I’ll distill key takeaways from these publications, highlighting essential strategies and best practices. I hope these insights prove valuable in shaping your security decisions and governance framework.
What is Data Security Governance?
Jonathan Reichental in “Data Governance for Dummies” says data security governance “is concerned with protecting data from unauthorized access, loss of integrity, or theft at any time in the life of the data.” For this reason, Gartner claims data security governance is vital as organizations recognize the intrinsic value of data as an asset and as regulators intensify their efforts to protect data. Gartner argues data security is driven by multiple factors, including expanding privacy and financial regulations, along with evolving legislation aimed at safeguarding sensitive information.
Read our blog “Data Security Governance: A Roadmap to Business Success” to learn more about what Data Security Governance is and how it can enhance data security strategies.
Why Does It Matter?
The growing reliance on cloud services has exposed the need for a data-centric approach to security. When organizations move to the cloud or share data with third parties, they lose control over their traditional perimeter defenses. Gartner argues that while cloud-native security controls can be effective for specific environments, they lack cross-platform compatibility and often require separate management consoles, complicating the security landscape.
Security architects for this reason face a challenge in defining appropriate controls, as organizations frequently struggle to articulate the value, usage, and protection needs for their data. This can lead to either overly restrictive or insufficient security measures, resulting in frustration and the perception that tools are ineffective. Moreover, data security is often embedded within broader solutions like web gateways and cloud access security brokers, rather than existing as a standalone market, which complicates consistent control application. While privacy regulations mandate tools like encryption and data loss prevention, Gartner argues “true privacy engineering demands far more than a few isolated security measures.”
Gartner Recommendations
Gartner argues for adopting a data-centric security architecture to ensure appropriate control over data use and protection. By focusing on data as an asset and its specific requirements, organizations can apply consistent security controls across diverse data silos and applications. This approach enables clear and effective data security governance.
A key part of DSG is understanding how different types of data vary in sensitivity. This allows organizations to achieve two critical goals: first, ensuring everyone who handles data is aware of how to treat it based on its classification, and second, empowering security architects, engineers, developers, and administrators to build solutions aligned with security standards rooted in these classifications. Sensitive data, such as personally identifiable information (PII) and intellectual property, demands higher levels of protection due to the reputational, legal, or financial risks associated with exposure. Effective data classification and categorization are essential for addressing common security questions like: How do I find PII? and How do I protect intellectual property? Failure to control data access can lead to severe outcomes, including exposure, ransomware attacks, or ineffective deployment of other security measures like data loss prevention (DLP). At the same time, it is important to recognize the complexity of user roles within organizations and that rules around PII cannot be a one size fits all.
Data access governance must encompass both structured and unstructured data, regardless of whether it resides in the cloud or on-premises. Implementing the principle of least privilege is crucial, with modern tools now bridging the gap between identity and access management and data security to ensure tighter, more effective control.
Who Owns DSG Or Who Should be Stakeholders
Ownership of DSG varies across organizations. In some cases, it falls under the Chief Data Officer (CDO), who oversees broader data governance efforts. In others, it is led by the Chief Information Security Officer (CISO), because of their focus on security governance, which prioritizes mitigating business risks through cybersecurity measures. According to Gartner, here cybersecurity teams manage risk and align risk with overall business objectives, often requiring joint leadership from both business and IT.
Regardless of who formally owns DSG, success depends on collaboration among senior executives, CDOs, and CISOs. This collective effort ensures that robust policies are implemented to safeguard the organization’s data and align security priorities with business needs. The challenge, as Gartner highlights, lies in communication. Security leaders often fail to express data security risks in terms that resonate with business leaders, which leads to underfunded data security programs and gaps in the security posture. This is likely to change under new SEC mandates, which now hold CFOs and CISOs accountable for assessing the material impact of data breaches, potentially fostering better collaboration between security teams and business executives.
How Can Privacera Help
Privacera offers a comprehensive end-to-end solution for managing data security governance across an increasingly hybrid IT data estate. The platform delivers holistic data visibility, secure access, and compliance, ensuring seamless collaboration across cloud and on-premises environments. Key benefits include a unified platform, automation of manual governance tasks, continuous improvement, and enhanced data stewardship through streamlined processes for sensitive data discovery and protection.
Privacera simplifies the data security landscape by eliminating the need for multiple, disjointed governance tools. Its automated data discovery identifies and classifies sensitive data across cloud and on-premises systems, using AI and machine learning to detect unprotected data and personally identifiable information (PII). Centralized access controls allow data stewards to define policies, automate workflows, and apply comprehensive access rules consistently across all data sources—ensuring compliance with regulations like GDPR, CCPA, and HIPAA.
The platform also supports the broadest range of data assets and integrates with identity management tools to optimize interoperability without impacting performance. Privacera’s encryption, masking, and federated authorization capabilities further enhance security, while comprehensive audit reporting provides detailed insight into data access, enabling both internal and external compliance efforts with ease. This centralized, automated solution empowers organizations to securely manage their data with consistency and precision.
In summary, its core capabilities include:
- Sensitive Data Discovery
- Comprehensive Data Access Management
- Data Encryption and Masking
- Sensitive Data Auditing and Reporting
These operate in the following fashion.
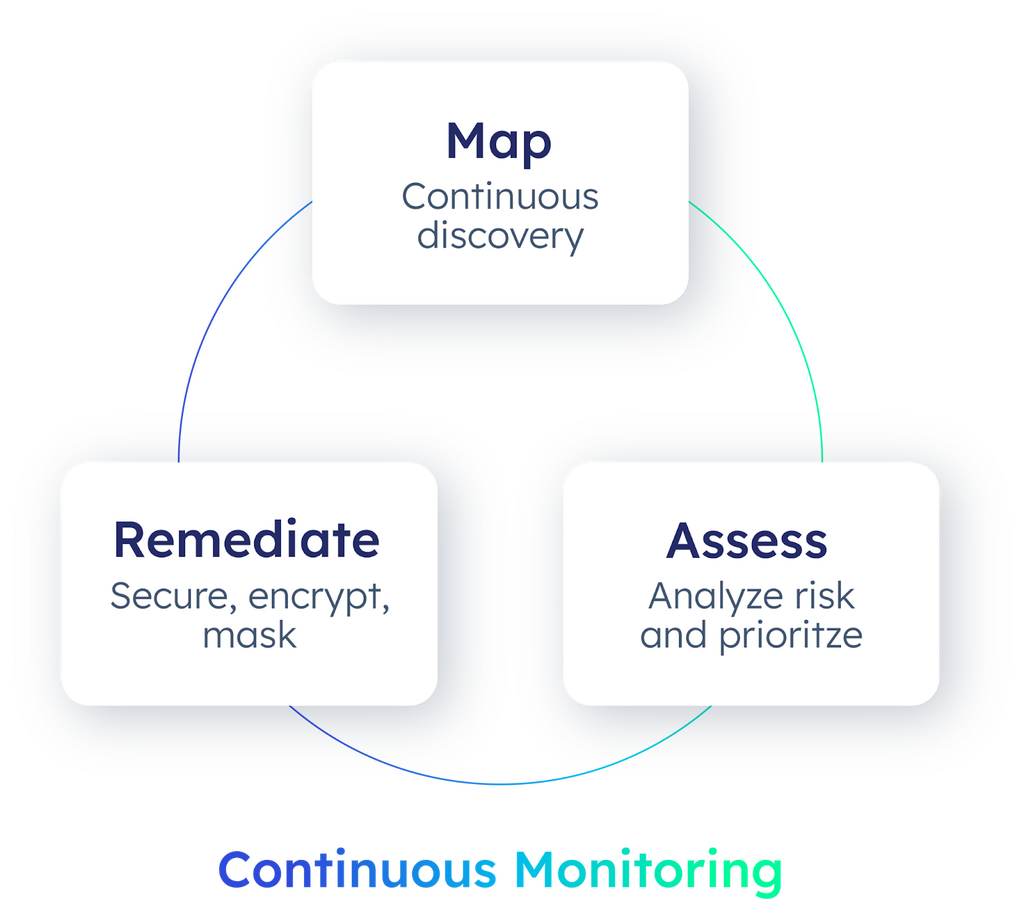
With Privacera’s data security platform, customers discover, classify, and tag sensitive enterprise data, both structured and unstructured, while visualizing where it resides, who can access it, and how it’s being used. Assess security risks by analyzing over-provisioning, assigning risk-based scores, and detecting risky access patterns. Remediate vulnerabilities through automated compliance workflows, refining access controls with fine-grained RBAC, ABAC, and TBAC models, and enhancing protection via data masking and encryption.
Popular Data Security Governance Use Cases
One of the key aspects of Gartner’s definition of the data security platform is that it contains various capabilities and as a result it supports various use cases. In Privacera we observe the following use cases or focus points that customers deploy our solutions for:
Data security posture management (DSPM): For many customers with data lake deployments with an element of regular data ingests from third parties or unknown data formats, the biggest first challenge is visibility into the data and whether it contains sensitive data. That identification and tagging can be simply informational for risk assessment or in some cases lead to the automatic application of tag-based controls before data is moved into an analytical zone. Customers have seen SLA improvements of up to 95% in data readiness for analytics and compliance.
Data access governance: This initiative is often led by data platform and infrastructure teams as part of modernization or migration efforts. The effort and risk of inconsistencies when managing access permissions and fine grained controls across a diverse data estate can be removed with a centralized DSP. Customers have seen a reduction of up to 90% in the time it takes to provision new data or new access requests.
Parting Words
Gartner continues to highlight the critical importance of data security governance as organizations navigate a rapidly evolving data landscape. With the rise of cloud services, privacy regulations, and emerging technologies like generative AI, the need for a robust, data-centric security framework has never been more pressing. Gartner stresses the importance of classifying data based on its sensitivity to ensure appropriate protection, empowering teams to make informed security decisions.
Privacera offers an all-in-one solution for managing data security governance across hybrid environments, simplifying the complexities of data protection. The platform automates sensitive data discovery, applies consistent security controls, and ensures compliance with privacy regulations. By centralizing governance tasks, Privacera helps organizations maintain security and streamline data stewardship, all while optimizing performance and scalability. To learn how Privacera can optimize your data security governance strategy, please request a demo here.





